WinRAR Vulnerability: How to Protect Yourself from Malware Attacks
WinRAR Vulnerability is a popular file archiver tool for Windows that has been around for over 20 years. It is used by millions of people around the world to compress and extract files. However, a recent vulnerability in WinRAR has been exploited by hackers to spread malware since April 2023.
The vulnerability, tracked as CVE-2023-38831, is a remote code execution (RCE) vulnerability that allows attackers to execute arbitrary code on a victim’s computer by exploiting a flaw in the way WinRAR processes ZIP files.
What is a WinRAR vulnerability?
A WinRAR vulnerability is a weakness in the software that attackers can exploit to gain unauthorized access to your system, steal data, install malware, or disrupt your computer’s operation. These vulnerabilities can exist in various parts of the software, such as the file parsing engine, archive processing routines, or user interface components.
A WinRAR is a weakness in the software that attackers can exploit to gain unauthorized access to your system, steal data, install malware, or disrupt your computer’s operation. These vulnerabilities can exist in various parts of the software, such as the file parsing engine, archive processing routines, or user interface components.
WinRAR Vulnerability: How the attack works
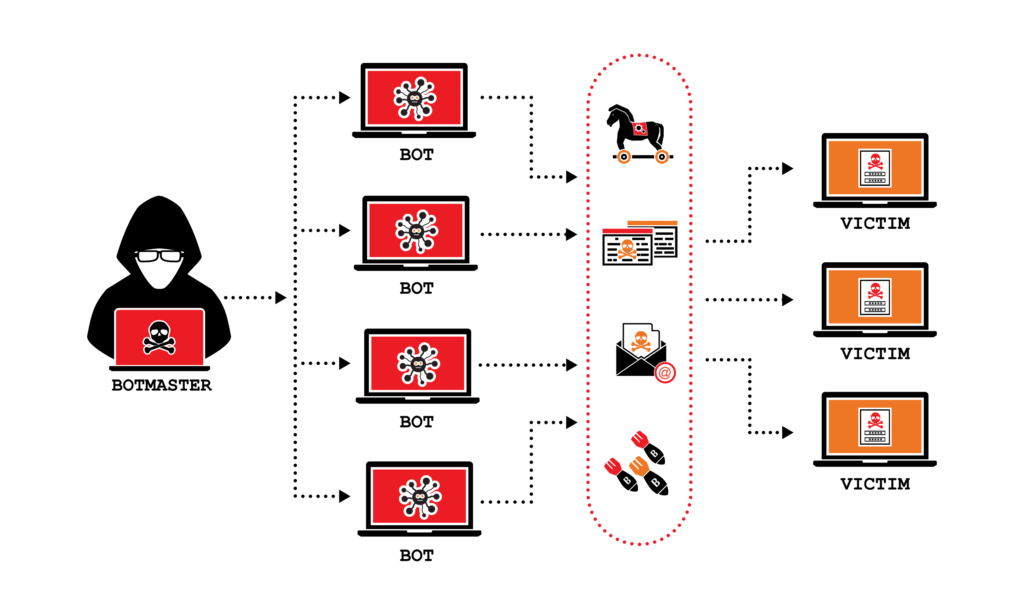
The attack typically works by tricking the victim into opening a malicious ZIP file. The ZIP file may contain a seemingly harmless file, such as a JPEG image or a text file. However, the ZIP file also contains a specially crafted file that exploits the vulnerability in WinRAR.
When the victim opens the ZIP file, WinRAR automatically extracts the files in the archive. This includes the specially crafted file that exploits the vulnerability. When WinRAR extracts the specially crafted file, it executes arbitrary code on the victim’s computer.
How to Protect Yourself from Malware Attacks 2024
1. Update WinRAR Immediately:
- Download and install the latest version of WinRAR from the official website: https://www.win-rar.com/
- Older versions may contain known vulnerabilities that attackers can exploit.
2. Scan for Existing Malware:
- Run a full system scan with a reputable antivirus or anti-malware program.
- This will detect and remove any malware that may already be present on your system due to previous exploitation.
3. Be Cautious with Downloaded Files:
- Only download files from trusted sources.
- Avoid opening attachments or links from unknown senders.
- Scan any downloaded files with your antivirus software before opening them.
4. Enable Enhanced Security Measures:
- Consider using a third-party security software that offers additional protection against vulnerabilities and malware attacks.
- Keep your operating system and other software updated with the latest security patches.
- Enable features like User Account Control (UAC) in Windows to restrict unauthorized program installations.
Additional Recommendations:
- Stay informed about the latest WinRAR vulnerabilities and security updates by visiting the official website or following reputable security news sources.
- Exercise caution when opening compressed files, even from trusted sources.
- Back up your important data regularly to prevent data loss in case of a malware attack.
- Consider using alternative file compression software if you have concerns about WinRAR’s security.
What kind of malware is being spread?
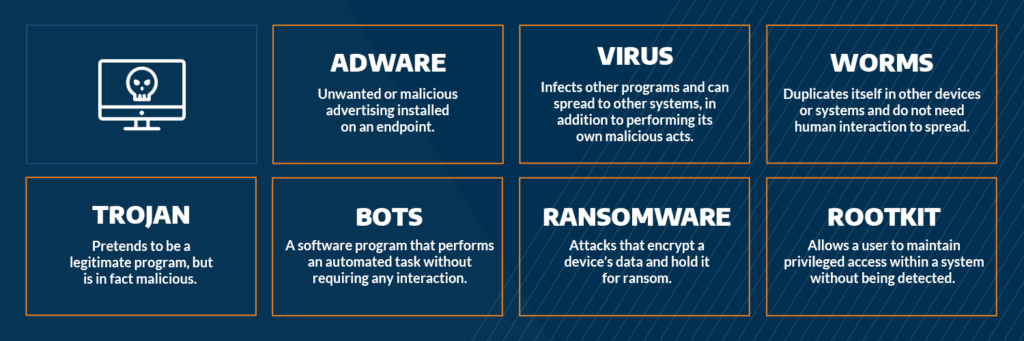
The vulnerability has been exploited to spread a variety of malware families, including DarkMe, GuLoader, and RemcosRAT. DarkMe is a malware family that is known for stealing financial information, such as credit card numbers and bank account numbers. GuLoader is a malware downloader that can be used to download other malware onto the victim’s computer. RemcosRAT is a remote access Trojan (RAT) that can be used by hackers to control the victim’s computer remotely.
WinRAR Vulnerability: Who is being targeted?
The attacks have been targeted at a variety of individuals and organizations, including financial traders, cryptocurrency exchanges, and government agencies.
WinRAR Vulnerability: How to protect yourself
There are a number of things you can do to protect yourself from this attack:
- Update your WinRAR software. WinRAR has released a patch for the vulnerability. You should update your WinRAR software to the latest version as soon as possible.
- Be careful about opening ZIP files from unknown sources. If you receive a ZIP file from someone you don’t know, don’t open it. Instead, contact the sender and ask if they really sent you the file.
- Use a security solution. A security solution can help to protect you from malware attacks. Make sure that your security solution is up to date and that it is enabled.
Are there any known WinRAR vlnerabilities right now?
How can I protect myself from WinRAR vulnerabilities?
Keep WinRAR updated: Regularly check for and install the latest updates for WinRAR. These updates often include security patches that fix vulnerabilities.
Be cautious with downloaded files: Only download files from trusted sources. Don’t open attachments or links from unknown senders, especially if they are in RAR format.
Use a strong antivirus and anti-malware program: Keep your antivirus software up to date and run regular scans. This can help detect and remove malware that may have been installed through a WinRAR vulnerability.
Enable advanced security features: Consider enabling features like User Account Control (UAC) in Windows to restrict unauthorized program installations.
Backup your data: Regularly back up your important data to prevent data loss in case of a malware attack.
What should I do if I think I’ve been infected with malware through a WinRAR vulnerability?
Disconnect from the internet: This will prevent the malware from spreading and communicating with attackers.
Run a full system scan with your antivirus or anti-malware program.
Consider wiping and reinstalling your operating system: This is the most thorough way to remove malware, but it will also erase all your data, so make sure you have backups.
Change your passwords for all your online accounts.
Should I stop using WinRAR altogether?
Additional Resources:
WinRAR website: https://www.rarlab.com/download.htm
National Vulnerability Database (NVD): https://nvd.nist.gov/
Cybersecurity & Infrastructure Security Agency (CISA): https://www.cisa.gov/
By understanding WinRAR vulnerabilities and taking necessary precautions, you can help protect yourself from cyberattacks and keep your system safe.
Conclusion
The vulnerability in WinRAR is a serious security issue that has been exploited by hackers to spread malware. It is important to update your WinRAR software to the latest version and to be careful about opening ZIP files from unknown sources.
Additional information
In addition to the above, here are some other things to keep in mind:
- Hackers are constantly developing new ways to exploit vulnerabilities, so it is important to stay informed about the latest security threats.
- You can do this by following security news websites and blogs, and by signing up for security alerts from trusted sources.
- If you are concerned about your security, you can also consult with a security professional.
Case studies
Here are some case studies of how the WinRAR vulnerability has been exploited in recent months:
- In April 2023, Group-IB researchers discovered that the vulnerability was being exploited to deliver DarkMe malware to financial traders. The DarkMe malware was used to steal financial information, such as credit card numbers and bank account numbers.
- In June 2023, Google’s Threat Analysis Group (TAG) discovered that the vulnerability was being exploited by government-backed groups to deliver malware to a variety of targets. The malware delivered by these groups included DarkMe, GuLoader, and RemcosRAT.
- In July 2023, researchers at Check Point discovered that the vulnerability was being exploited to deliver malware to cryptocurrency exchanges. The malware delivered by these groups was used to steal cryptocurrency wallets.
Recommendations
To protect yourself from this attack, we recommend the following:
- Update your WinRAR software to the latest version.
- Be careful about opening ZIP files from unknown sources.
- Use a security solution to help protect you from malware attacks.
- Stay informed about the latest security threats.
- Consult with a security professional if you are concerned about your security.








Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
welcome
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.